Q: I was analyzing the 30 days malware log file and found hundreds of "BKDR_Generic.DIT" and "TROJ_Generic.DIT" which stated questionable action result - Passed Potential Security Risk. I am sure that I have already enabled Generic Detection by adding few lines in the ofcscan.ini. Anything to worry about?
A: You have done the right thing by enabling generic detection. The purpose of this detection is to make us aware that there is a certain file that is posing some threats. There is a big possibility that this is malicious file. We are just letting it pass because we do not have still an enhanced clean pattern for that one. If we quarantine or delete that file, it is very risky. Why? It is because the file could be a system file or a .dll file that is an important file on Windows. If we quarantine/delete it, there is a chance that your Windows will hang or even BSOD.
The moment you are aware of such generic virus. The next step is to collect them. Compress the files using WinZip and put a password: virus. Send the sample files to us and we will create an enhanced pattern file for you. Also, it will be much better if you use our SIC Tool to further analyze your system for other infections. Then send the sic logs and suspect.zip. Furthermore, send the Virus logs for us to know who are being infected and find the PC that is the one infecting the system.
I hope this helps.
Showing posts with label OSCE. Show all posts
Showing posts with label OSCE. Show all posts
Wednesday, April 14, 2010
Monday, April 12, 2010
OSCE SP1 ; found encrypted as the action in malware log
q: I found "encrypted" as the result action in malware log for OSCE 10 with SP1
a: This is is a new feature in OfficeScan 10, where the virus logs will show an "encrypted" result. The "Encrypted" result happens when the Scan Engine (VSAPI) is unable to take action (quarantine, delete, rename) on a malware. Instead, the OfficeScan client will just encrypt the malware.
a: This is is a new feature in OfficeScan 10, where the virus logs will show an "encrypted" result. The "Encrypted" result happens when the Scan Engine (VSAPI) is unable to take action (quarantine, delete, rename) on a malware. Instead, the OfficeScan client will just encrypt the malware.
Friday, March 19, 2010
OSCE 10 client with smart scan method
I hope this answers you (you know who you are) :-)
If your OSCE 10 client is using smart scan method, you can view the following from component version when you right click the OSCE client icon in system tray.

Notice there is no conventional pattern file version (lpt$vpn###)
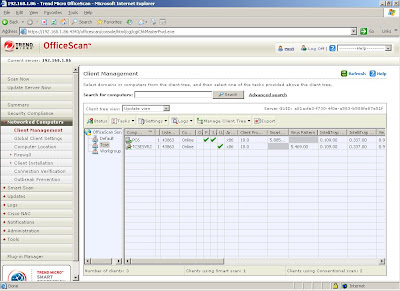
Refer below for the view from OSCE web console. It will show either conventional pattern file or smart scan agent pattern.
Hope this helps!
If your OSCE 10 client is using smart scan method, you can view the following from component version when you right click the OSCE client icon in system tray.

Notice there is no conventional pattern file version (lpt$vpn###)
Refer below for the view from OSCE web console. It will show either conventional pattern file or smart scan agent pattern.

Hope this helps!
Monday, February 22, 2010
Install Patch 5 for OSCE 8 to support for Windows 7 clients
Wednesday, January 20, 2010
virus log from OSCE 10 client
q: Where to obtain the physical file of the virus log from your client pc?
a: go to the officescan client installation, look for MISC folder. The content is all logs related ; virus log, spyware log
a: go to the officescan client installation, look for MISC folder. The content is all logs related ; virus log, spyware log
Thursday, November 12, 2009
What is 'Infection source'?

You can see this from your OfficeScan virus logs.
You may not have the Infection Source if the infection is of trojan, generic malware or backdoor. Most cases in worm typically network worm you will have Infection Source information. Some virus detection doesn't have Infection Source if the infection is local meaning it is not coming from a remote computer. Also, it doesn't require scanning of mapped drives to check or detect infection source since the detection of infection source is based on the NET SESSION on the local computer.
For example, if User A accesses a virus infected share on User B's machine, User B will become listed in the Infected Sources list.
If there are no sources on the private network sharing malware, then nothing will be shown.
Wednesday, November 11, 2009
OSCE 8.0 and Windows 7
Question:
I have OSCE 8.0 installed in my environment. Is there any patch available to support for Windows 7 client OS?
Answer:
No. You have to upgrade to version 10 in order to support Windows 7. If your license is still valid, you are entitled for free upgrade.
I have OSCE 8.0 installed in my environment. Is there any patch available to support for Windows 7 client OS?
Answer:
No. You have to upgrade to version 10 in order to support Windows 7. If your license is still valid, you are entitled for free upgrade.
Monday, November 2, 2009
Support for Windows 7, both OSCE and WFBS
Wednesday, October 28, 2009
Activating your OSCE 10 with superkey
Issue:
I have my paper license with the following description:
OfficeScan Superkey (AV+SW+DC+FW)English ver 10.x
I'm upgrading my OSCE 8 to OSCE 10. During the installation wizard, I put in the superkey for the first item which is for antivirus module only. refer below screen shot.

Once upgrade is done, from the web console Administration > Product License under License Information table I can see that "Antivirus for Desktop" and "Antivirus for Servers" both in grace period. The other services "Web Reputation and Anti-Spyware for desktops", "Web Reputation and Anti-Spyware for Servers" and "Damage Cleanup Services" shown as not activated.
What went wrong?
Solution:
Login to the web console. Click on Administration > Product License. Choose the services for which you want to activate or refresh the license information.
There are two things here:
1. For License appear as in grace period or expired despite the license just renewed. This is because you have to update information upon renewing the license. This will allow for the OSCE server to sync with the License Server for the new expiry date, license seats number and other relevant information. Refer to below screen shot. You will have to click on the "Update Information" button.
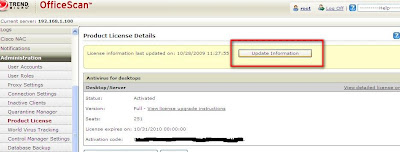
2. Activating Web Reputation and Damage Cleanup Services for OSCE 10 is actually by using the same key. Hence the name SuperKey. Don't forget to click on the "Update Information" button once you are done.
I have my paper license with the following description:
OfficeScan Superkey (AV+SW+DC+FW)English ver 10.x
I'm upgrading my OSCE 8 to OSCE 10. During the installation wizard, I put in the superkey for the first item which is for antivirus module only. refer below screen shot.

Once upgrade is done, from the web console Administration > Product License under License Information table I can see that "Antivirus for Desktop" and "Antivirus for Servers" both in grace period. The other services "Web Reputation and Anti-Spyware for desktops", "Web Reputation and Anti-Spyware for Servers" and "Damage Cleanup Services" shown as not activated.
What went wrong?
Solution:
Login to the web console. Click on Administration > Product License. Choose the services for which you want to activate or refresh the license information.
There are two things here:
1. For License appear as in grace period or expired despite the license just renewed. This is because you have to update information upon renewing the license. This will allow for the OSCE server to sync with the License Server for the new expiry date, license seats number and other relevant information. Refer to below screen shot. You will have to click on the "Update Information" button.

2. Activating Web Reputation and Damage Cleanup Services for OSCE 10 is actually by using the same key. Hence the name SuperKey. Don't forget to click on the "Update Information" button once you are done.
Wednesday, October 14, 2009
Worry Free installed on Apache Web Server
Issue/concern:
A customer installed Worry Free on Apache Web Server rather than IIS. Now, he is concern since he is going to patch the Apache whether it will affect the Worry Free web console installation. Is there anything to backup?
Answer:
Well actually nothing to backup on WFBS just make sure you have an apache backup. Just incase you need to revert back. Check the apache update’s roll back procedure as well if thre’s any.
On our documentation we can support Apache ver 2.0.63 or later. As long as you are on the range I see no harm.
Allow me to put some of my thoughts into this, although apache is nice and stable Web server we only included it in the package if a client with limited machineries would like to install the product on a non windows server class OS. I suggest you use IIS instead.
Note: you might want to consider backup httpd.conf, c:\etc. For more infor you may google around. :-)
A customer installed Worry Free on Apache Web Server rather than IIS. Now, he is concern since he is going to patch the Apache whether it will affect the Worry Free web console installation. Is there anything to backup?
Answer:
Well actually nothing to backup on WFBS just make sure you have an apache backup. Just incase you need to revert back. Check the apache update’s roll back procedure as well if thre’s any.
On our documentation we can support Apache ver 2.0.63 or later. As long as you are on the range I see no harm.
Allow me to put some of my thoughts into this, although apache is nice and stable Web server we only included it in the package if a client with limited machineries would like to install the product on a non windows server class OS. I suggest you use IIS instead.
Note: you might want to consider backup httpd.conf, c:\etc. For more infor you may google around. :-)
Tuesday, October 6, 2009
iCrcPtnDP log file
Issue:
Customer installed OSCE 10, with smart scan scanning method.
Recently, he found out that in this particular folder .\PCCSRV\log folder there are many logs by the name iCrcPtnDPxxxxxx.log (e.g. iCrcPtnDP647700.log). If this continues they are worried that it might used up the HDD space a lot.
Is this log important?
Answer:
This log is just icrc pattern update logs (server smart scan). It is safe to just delete the log from time to time.
I hope it helps.
Customer installed OSCE 10, with smart scan scanning method.
Recently, he found out that in this particular folder .\PCCSRV\log folder there are many logs by the name iCrcPtnDPxxxxxx.log (e.g. iCrcPtnDP647700.log). If this continues they are worried that it might used up the HDD space a lot.
Is this log important?
Answer:
This log is just icrc pattern update logs (server smart scan). It is safe to just delete the log from time to time.
I hope it helps.
Friday, September 11, 2009
Improving the performance of OfficeScan related clients agents
You notice poor performance from any of the following:
OfficeScan 7.0 / 7.3 / 8.0 / 10 client
Client Server Messaging Security for SMB (CSM) 3.x Agent
Worry-Free Business Security (WFBS) Standard / Advanced Agent
Please refer to this knowledge base.
1. As a workaround, disable the TSC.exe process from starting at startup
2. If the issue persists, delay the RealTimeScan process from starting at startup
3. If the issue still persists, resize the "PagedPoolSize" registry key
4. If this does not work, run the Case Diagnostic Tool (CDT)
OfficeScan 7.0 / 7.3 / 8.0 / 10 client
Client Server Messaging Security for SMB (CSM) 3.x Agent
Worry-Free Business Security (WFBS) Standard / Advanced Agent
Please refer to this knowledge base.
1. As a workaround, disable the TSC.exe process from starting at startup
2. If the issue persists, delay the RealTimeScan process from starting at startup
3. If the issue still persists, resize the "PagedPoolSize" registry key
4. If this does not work, run the Case Diagnostic Tool (CDT)
Friday, September 4, 2009
List of endpoint security software that OSCE automatically uninstalls
This is related to old entry with the topic 'Removal of antivirus product during OSCE installation'.
I came across the below note while reading the Student Textbook for OSCE 10, TCSE course. Thought of sharing it.
"If Trend Micro or third-party endpoint security programs are installed on the computer, check if OfficeScan can automatically uninstall the software and replace it with the OfficeScan client. For a list of endpoint security software that OfficeScan automatically uninstalls, open the following files in {installation path}\PCCSRV\Admin. You can open these files with a text editor like Notepad.
tmuninst.ptn
tmuninst_as.ptn
If the software on the target computer is not included in the list, manually uninstall it first. "
I came across the below note while reading the Student Textbook for OSCE 10, TCSE course. Thought of sharing it.
"If Trend Micro or third-party endpoint security programs are installed on the computer, check if OfficeScan can automatically uninstall the software and replace it with the OfficeScan client. For a list of endpoint security software that OfficeScan automatically uninstalls, open the following files in {installation path}\PCCSRV\Admin. You can open these files with a text editor like Notepad.
tmuninst.ptn
tmuninst_as.ptn
If the software on the target computer is not included in the list, manually uninstall it first. "
Thursday, July 23, 2009
OSCE 8.0 hotfix 3300
Overview of this hotfix release
enables the OSCE client to control access to external devices. e.g to disable the autorun feature for USB device
note:
- you will not be able to run the hotfix, if it detects your OSCE build doesn't meet the requirement
- supported only on 32bit platforms
- please perform the post installation configuration.
- the device access control feature (DAC) applies to all clients.
- OSCE client will not report unauthorized access logs to the OSCE server. However, user can look for the logs locally in the client machine located at ../Trend Micro/BM/Log
where to get the hotfix?
you may request it from Trend Support.
suggestion for post installation configuration (modify and add to ofcscan.ini). This parameter will just enable the disabling autorun for USB devices.
########################start####################################
[Global Setting]
EnableAEGIS=1
CheckMountPointInterval=300
[AEGIS_DACPolicy]
#PolicyId0=D001 - Device Access Control On Plug in devices (USB)
#PolicyId0=D002 - Device Access Control On CD/DVD
#PolicyId0=D003 - Device Access Control On FLOPPY
#PolicyId0=D004 - Device Access Control On Network Resource
#PolicyId0=D005 - Block AutoRun function on USB devices
# v=0 (disable), 1 (enable)
# w=0 (no pop up), 1 (allow pop up)
# x=0 (pass), 2 (deny access), 4 (Read Only), 5 (Read & Write only), 6 (Read & Execute only)
# y=0 (pass), 2 (deny access)
# z=0 (disable), 1 (enable)
Count=5
Enable=1
PopAlert=0
PolicyId0=D001
Action0=5
Enable0=0
PolicyId1=D002
Action1=0
Enable1=0
PolicyId2=D003
Action2=0
Enable2=0
PolicyId3=D004
Action3=0
Enable3=0
PolicyId4=D005
Action4=2
Enable4=1
########################end####################################
enables the OSCE client to control access to external devices. e.g to disable the autorun feature for USB device
note:
- you will not be able to run the hotfix, if it detects your OSCE build doesn't meet the requirement
- supported only on 32bit platforms
- please perform the post installation configuration.
- the device access control feature (DAC) applies to all clients.
- OSCE client will not report unauthorized access logs to the OSCE server. However, user can look for the logs locally in the client machine located at ../Trend Micro/BM/Log
where to get the hotfix?
you may request it from Trend Support.
suggestion for post installation configuration (modify and add to ofcscan.ini). This parameter will just enable the disabling autorun for USB devices.
########################start####################################
[Global Setting]
EnableAEGIS=1
CheckMountPointInterval=300
[AEGIS_DACPolicy]
#PolicyId0=D001 - Device Access Control On Plug in devices (USB)
#PolicyId0=D002 - Device Access Control On CD/DVD
#PolicyId0=D003 - Device Access Control On FLOPPY
#PolicyId0=D004 - Device Access Control On Network Resource
#PolicyId0=D005 - Block AutoRun function on USB devices
# v=0 (disable), 1 (enable)
# w=0 (no pop up), 1 (allow pop up)
# x=0 (pass), 2 (deny access), 4 (Read Only), 5 (Read & Write only), 6 (Read & Execute only)
# y=0 (pass), 2 (deny access)
# z=0 (disable), 1 (enable)
Count=5
Enable=1
PopAlert=0
PolicyId0=D001
Action0=5
Enable0=0
PolicyId1=D002
Action1=0
Enable1=0
PolicyId2=D003
Action2=0
Enable2=0
PolicyId3=D004
Action3=0
Enable3=0
PolicyId4=D005
Action4=2
Enable4=1
########################end####################################
Tuesday, July 14, 2009
OSCE 8.0 SSO login frm TMCM 3.5
issue:
My customer installed TMCM 3.5 and OSCE 8.0. OSCE 8.0 is currently registered to TMCM 3.5 as one of the agents.
OSCE web console url is non-ssl based. When try to access OSCE console from TMCM, TMCM will actually refer to ssl based of the OSCE url and result in broken link since OSCE is actually published at http:// instead of https://
How can this be fixed? User wants to SSO to OSCE console from TMCM 3.5. But her OSCE is http based where as TMCM trying to reach to https based of the URL.
SOlution:
Regarding this, kindly perform the following to have the Officescan run on HTTPS:
1. Unregister Officescan from TMCM and delete the entity as well on the TMCM directory tree
2. On the Officescan server open a command prompt and go to the following folder
C:\Program Files\Trend Micro\Officescan\PCCSRV\
3. Run the following command
svrsvcsetup -enablessl
4. Kindly check if you can now access the Officescan console using HTTPS
5. Register it now to TMCM
6. Kindly check if you can now peform SSO onto TMCM
My customer installed TMCM 3.5 and OSCE 8.0. OSCE 8.0 is currently registered to TMCM 3.5 as one of the agents.
OSCE web console url is non-ssl based. When try to access OSCE console from TMCM, TMCM will actually refer to ssl based of the OSCE url and result in broken link since OSCE is actually published at http://
How can this be fixed? User wants to SSO to OSCE console from TMCM 3.5. But her OSCE is http based where as TMCM trying to reach to https based of the URL.
SOlution:
Regarding this, kindly perform the following to have the Officescan run on HTTPS:
1. Unregister Officescan from TMCM and delete the entity as well on the TMCM directory tree
2. On the Officescan server open a command prompt and go to the following folder
C:\Program Files\Trend Micro\Officescan\PCCSRV\
3. Run the following command
svrsvcsetup -enablessl
4. Kindly check if you can now access the Officescan console using HTTPS
5. Register it now to TMCM
6. Kindly check if you can now peform SSO onto TMCM
Wednesday, July 8, 2009
OSCE SSO from TMCM 3.5
problem:
My customer installed TMCM 3.5 and OSCE 8.0 where OSCE 8.0 is currently registered to TMCM 3.5 as one of the agents.
OSCE web console url is non-ssl based. When try to access OSCE console from TMCM, TMCM will actually refer to ssl based of the OSCE url and result in broken link since OSCE is actually published at http:// instead of https://
How can this be fixed? User wants to SSO to OSCE console from TMCM 3.5. But her OSCE is http based where as TMCM trying to reach to https based of the URL.
answer:
Regarding this, kindly perform the following to have the Officescan run on HTTPS:
1. Unregister Officescan from TMCM adn delete teh entuty as well on the TMCM directory tree 2. On the Officescan server open a command prompt and go to the following folder
C:\Program Files\Trend Micro\Officescan\PCCSRV\
3. Run the following command
svrsvcsetup -enablessl
4. Kindly check if you can now access the Officescan console using HTTPS 5. Register it now to TMCM
My customer installed TMCM 3.5 and OSCE 8.0 where OSCE 8.0 is currently registered to TMCM 3.5 as one of the agents.
OSCE web console url is non-ssl based. When try to access OSCE console from TMCM, TMCM will actually refer to ssl based of the OSCE url and result in broken link since OSCE is actually published at http://
How can this be fixed? User wants to SSO to OSCE console from TMCM 3.5. But her OSCE is http based where as TMCM trying to reach to https based of the URL.
answer:
Regarding this, kindly perform the following to have the Officescan run on HTTPS:
1. Unregister Officescan from TMCM adn delete teh entuty as well on the TMCM directory tree 2. On the Officescan server open a command prompt and go to the following folder
C:\Program Files\Trend Micro\Officescan\PCCSRV\
3. Run the following command
svrsvcsetup -enablessl
4. Kindly check if you can now access the Officescan console using HTTPS 5. Register it now to TMCM
Friday, June 12, 2009
Removal of other antivirus product brand during OSCE installation
Question:
Will OSCE installer, automatically remove Microsoft Forefront?
Answer:
It will not automatically remove Microsoft Forefront anti-virus software.
I would suggest for you to manually uninstall the Microsoft Forefront antivirus and after that, kindly install the OfficeScan anti-virus software.
Actually, when OfficeScan client is installed, it automatically removes the following products first:
1. Authentium(TM) Command AntiVirus for Windows Enterprise 4.9x
2. Computer Associates (CA) eTrust(TM) Antivirus 8.1.655
3. eScan(TM) for Windows 8.0.653.1
4. ESET(TM) NOD32(TM) Antivirus build 3.0.642
5. ESET(TM) NOD32(TM) Antivirus 3.0.667.0
6. Kaspersky(TM) Anti-Virus 6.0.3.837
7. McAfee(TM) Total Protection
8. McAfee ePolicy Agent 3.6.0.574
9. McAfee VirusScan Enterprise 8.7.0.570
10. Norman(TM) Virus Control 5.99.0600
11. Symantec(TM) 11.0.780.1109 Endpoint Protection
12. Symantec 11.0.2010.25 Endpoint Protection MR 2
13. Symantec Endpoint Protection 11.0.3001.2224
14. Symantec Endpoint Protection 11.0.4000.2295
15. Symantec 11.0.4000.2295 Endpoint Protection 64-bit Edition
Hope this info helps.
Will OSCE installer, automatically remove Microsoft Forefront?
Answer:
It will not automatically remove Microsoft Forefront anti-virus software.
I would suggest for you to manually uninstall the Microsoft Forefront antivirus and after that, kindly install the OfficeScan anti-virus software.
Actually, when OfficeScan client is installed, it automatically removes the following products first:
1. Authentium(TM) Command AntiVirus for Windows Enterprise 4.9x
2. Computer Associates (CA) eTrust(TM) Antivirus 8.1.655
3. eScan(TM) for Windows 8.0.653.1
4. ESET(TM) NOD32(TM) Antivirus build 3.0.642
5. ESET(TM) NOD32(TM) Antivirus 3.0.667.0
6. Kaspersky(TM) Anti-Virus 6.0.3.837
7. McAfee(TM) Total Protection
8. McAfee ePolicy Agent 3.6.0.574
9. McAfee VirusScan Enterprise 8.7.0.570
10. Norman(TM) Virus Control 5.99.0600
11. Symantec(TM) 11.0.780.1109 Endpoint Protection
12. Symantec 11.0.2010.25 Endpoint Protection MR 2
13. Symantec Endpoint Protection 11.0.3001.2224
14. Symantec Endpoint Protection 11.0.4000.2295
15. Symantec 11.0.4000.2295 Endpoint Protection 64-bit Edition
Hope this info helps.
Tuesday, June 9, 2009
OSCE patch installation failed!
Question:
I have tried to install few patches for a customer's OSCE server which runs on x64 Windows 2003 server. The error is "Installation Failed!". One of the patches, OSCE_80_WinSP1_Patch2. It's just rollback and the build number from web console > about still shows version 3013. Even after server reboot.
What went wrong? Need your advice. Attached is the tmpatch.log
Answer:
Here is the analysis of the tmpatch.log (***note that it might vary depends on the case)
The patch installation failed because some files cannot be replaced.
Error Log:
----------------------------
[2009-06-08:16:05:26][cgiRecvFile.exe : C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp\1\pftB~tmp\FileGroup9\cgiRecvFile.exe->C:\Program Files (x86)\Trend Micro\OfficeScan\PCCSRV\Web_OSCE\Web\CGI\cgiRecvFile.exe fail]
Fail.
----------------------------
From the log above, the installation failed because the installer is unable to replace the file 'cgiRecvFile.exe'.
Try doing the following:
1. Stop OfficeScan service
2. Rename cgiRecvFile.exe to cgiRecvFile.exe.bak
**This file can be found on C:\Program Files (x86)\Trend Micro\OfficeScan\PCCSRV\Web_OSCE\Web\CGI\
3. Then try to install the patch again.
If problem persist, please check the updated tmpatch.log!
I have tried to install few patches for a customer's OSCE server which runs on x64 Windows 2003 server. The error is "Installation Failed!". One of the patches, OSCE_80_WinSP1_Patch2. It's just rollback and the build number from web console > about still shows version 3013. Even after server reboot.
What went wrong? Need your advice. Attached is the tmpatch.log
Answer:
Here is the analysis of the tmpatch.log (***note that it might vary depends on the case)
The patch installation failed because some files cannot be replaced.
Error Log:
----------------------------
[2009-06-08:16:05:26][cgiRecvFile.exe : C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp\1\pftB~tmp\FileGroup9\cgiRecvFile.exe->C:\Program Files (x86)\Trend Micro\OfficeScan\PCCSRV\Web_OSCE\Web\CGI\cgiRecvFile.exe fail]
Fail.
----------------------------
From the log above, the installation failed because the installer is unable to replace the file 'cgiRecvFile.exe'.
Try doing the following:
1. Stop OfficeScan service
2. Rename cgiRecvFile.exe to cgiRecvFile.exe.bak
**This file can be found on C:\Program Files (x86)\Trend Micro\OfficeScan\PCCSRV\Web_OSCE\Web\CGI\
3. Then try to install the patch again.
If problem persist, please check the updated tmpatch.log!
Wednesday, May 20, 2009
IDS-SYN flood in the OSCE firewall log
Question/Concern/Inquiry:
Hi, I received this OfficeScan logs from my customer asking why there are lots of entries on IDS-SYN flood. How to fix this? Is it because of the machine is infected or not properly patch? Please help to clarify.

Solution/Recommendation:
Two hosts use a SYN FLOOD packet to "shake hands" before establishing a TCP connection. During an attempt to connect, some of the target machine’s resources, such as the memory, may be in use so it does accept the request.
Some attacks take advantage of this TCP feature to flood the target machine with requests that it cannot process. These are called half-open sessions and is a type of Denial of Service (DoS) attack. The connection count between 172.16.1.13 and 168.168.1.186 exceed the default value 64,and this trigger the SYNFLOOD IDS filter.
This is a design specification because of the default SynfloodHalpOpen count is set to 64, if the connection count exceed, IDS rules will be trigged. You can check with the administrators of the company to check why it is sending TCP flood connections by using packet capture (wireshark).
We can also change OSCE Client setting to enlarge the SYNFLOOD halfopen count to workaround: Find the following key: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\tmcfw\Parameters\ IdsSynFloodHalfOpen (DWORD): Default 64 IdsSynFloodSynPerSec (DWORD): Default 4 Change IdsSynFloodHalfOpen to 256 If they still encounter a problem, change IdsSynFloodHalfOpen to 512
Hope this helps.
Hi, I received this OfficeScan logs from my customer asking why there are lots of entries on IDS-SYN flood. How to fix this? Is it because of the machine is infected or not properly patch? Please help to clarify.

Solution/Recommendation:
Two hosts use a SYN FLOOD packet to "shake hands" before establishing a TCP connection. During an attempt to connect, some of the target machine’s resources, such as the memory, may be in use so it does accept the request.
Some attacks take advantage of this TCP feature to flood the target machine with requests that it cannot process. These are called half-open sessions and is a type of Denial of Service (DoS) attack. The connection count between 172.16.1.13 and 168.168.1.186 exceed the default value 64,and this trigger the SYNFLOOD IDS filter.
This is a design specification because of the default SynfloodHalpOpen count is set to 64, if the connection count exceed, IDS rules will be trigged. You can check with the administrators of the company to check why it is sending TCP flood connections by using packet capture (wireshark).
We can also change OSCE Client setting to enlarge the SYNFLOOD halfopen count to workaround: Find the following key: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\tmcfw\Parameters\ IdsSynFloodHalfOpen (DWORD): Default 64 IdsSynFloodSynPerSec (DWORD): Default 4 Change IdsSynFloodHalfOpen to 256 If they still encounter a problem, change IdsSynFloodHalfOpen to 512
Hope this helps.
Monday, May 18, 2009
OSCE 10 is here!
The OfficeScan 10.0 GM build 1068R1 was posted on the Trend Micro website on May 15th as scheduled. This GA build is the same as the one that was uploaded to the Beta FTP server for all Beta participants to download.
Note: Due to an issue with the original OfficeScan 10.0 GA product package available for download from the Trend site early on May 15th, you may have encountered the following error when trying to install OfficeScan 10.0.
“Program too big to fit in memory"
This issue has now been resolved. If you encountered this error please download the current package from the Trend website.
http://www.trendmicro.com/download/product.asp?productid=5
Note: Due to an issue with the original OfficeScan 10.0 GA product package available for download from the Trend site early on May 15th, you may have encountered the following error when trying to install OfficeScan 10.0.
“Program too big to fit in memory"
This issue has now been resolved. If you encountered this error please download the current package from the Trend website.
http://www.trendmicro.com/download/product.asp?productid=5
Subscribe to:
Posts (Atom)
